“All of your files are encrypted with RSA-2048 and AES-128 ciphers” – RSA-2048/AES-128 ransomware
RSA-2048/AES-128 makes a very strong combination of crypto schemes.
Even if applied on stand-alone basis, those tools readily withhold your data so that any brute-forcing is just a waste of time. Now, the crooks have applied the two scripts at once. One of these serves to ensure the data remains affected for good, meaning the data stored within the file. The other aims at the filename. The victims cannot distinguish between the affected items, yet cannot open one to see what is within.
The virus creates an alert titled as follows:
‘All of your files are encrypted with RSA-2048 and AES-128 ciphers’
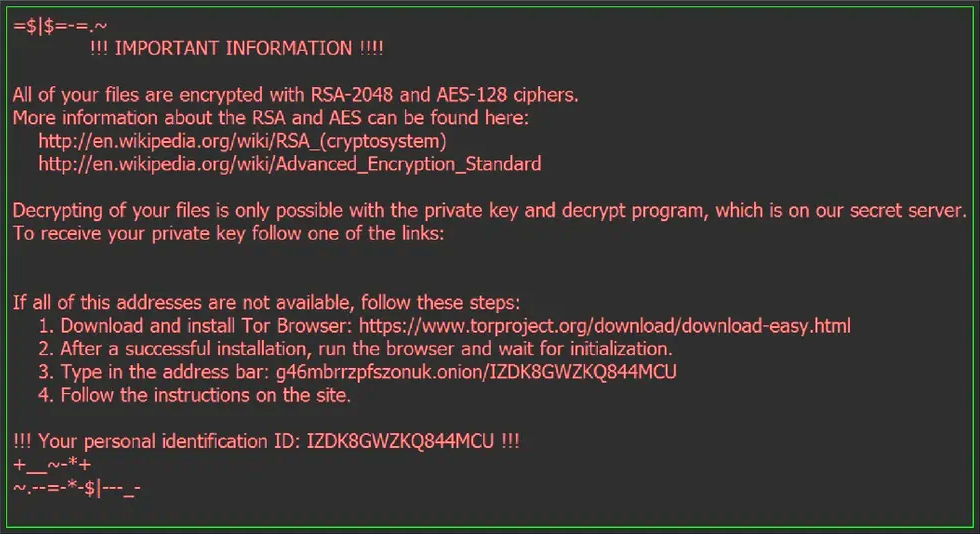
That is how the users are supposed to learn what is going on. Further part of the message by the ransomware instructs the victims that the salvation is only available with the decrypt program. The tool needs to be purchased; otherwise, the crooks promise to keep your data scrambled for good.
The virus does not hide its alert. It tries to hack Windows desktop. Consequentially, one is going to face the alert as a desktop background. Even if the desktop hack has failed, the message is anyway available in a TXT file. You will find that message within any directory along the files hit by the infection.
The message redirects to the Locky Decrypter page. That would say you need to purchase some 0.5 BTC and transfer the amount to the wallet specified. The transferring, once competed, shall trigger the process dispatching the key and decrypting software. The software use the key to decode the data name and subject matter. Thereby, the RSA-2048/AES-128 is actually the way the users concerned refer to Locky ransomware. As such, RSA-2048 and AES-128 are encryption tools. Those tools may both protect your data from impacts of the malefactors or simply ensure privacy thereof; meanwhile, the crooks too often abuse the advanced encryption systems pointing the crypto-gun at the innocent.
There are some workarounds that may help those in need to get rid of RSA-2048/AES-128 encryption attack; despite these cannot provide the ultimate decryptor, you may be rather satisfied with the outcome as you enjoy late enough copies of the files affected.
How to remove RSA-2048/AES-128 encryptor:
Step 1: Automated cleanup to remove RSA-2048/AES-128 ransomware
Step 2: Restore the encrypted files
Step 3: Shadow Volume Copies
Step 4: Backups
Automated cleanup to remove RSA-2048/AES-128 virus
Infection vector for ransomware typically features a trojan. The one in question definitely subscribes to that routine. The trojan drops its body into target computer and proceeds with disabling the detecting functionality of any security solution installed. The antivirus is thus unable to spot introduction of virus from the remote server.
The ransomware invasion is indicative of its dropper residing in the computer memory. It also hints at other invasions. The PC can hardly be considered properly protected due to the impacts of the above trojan.
Ultimate option implies a total formatting for any drives of your PC. That is not an option for many users, for it destroys all the data hosted by the machine. The best solution to pick would be in-depth system examination with a reliable security suite.
The trojan that has installed RSA-2048/AES-128 ransomware, unless removed, is to trigger its installation campaign as soon as a new strain of ransomware is available. Thereby, it is critical to kill it as soon as possible.
It is good to note the removal of RSA-2048/AES-128 ransomware does not recover the data affected. However, the virus is subject to compulsory extermination or else is going to introduce related infections into the machine.
Restore the encrypted files
RSA-2048/AES-128 ransomware encryption is a sophisticated data modification. There is no simple and single solution to cover all the cases. Transferring the ransom as demanded by the crooks is not the way either.Kindly apply the methods outlined below as they have been carefully developed to provide a recovery help for the most severe cases of encrypting assaults.
Good news is that the virus actually deals with copies of the files. The originals have been deleted. The removed data still can be restored using automatic data recovery tools.
Shadow Volume Copies
As Windows creates backups at given periods of time, a victim is advised to address relevant restore points. Unfortunately, the method cannot apply unless the System Restore had been enabled prior to the invasion. Please also note the recovery returns files as saved before the time associated with the restore point addressed.
Previous Versions dialog to target individual files
One can open Properties for any file. The menu has a tab called Previous Versions. It indicates versions of a file that have been backed up.
To make use of the feature, right-click an affected file and choose Properties in the drop-down list. Proceed with clicking the above-mentioned tab. You can opt between the Copy or Restore procedures, the former enabling to copy the item into the location specified by the user.
ShadowExplorer to accelerate the file-by-file recovery
Evidently, the routine above is quite laborious. Download and install the application called ShadowExplorer. It offers Export feature for much faster retrieval of the latest readable copies.
Backups
Prevention is the best cure. If you stick to making regular reserve copies of your data and store those outside your operating system, the impacts by the ransomware are very limited. However, prior to copying the data from backups into the system hit by RSA-2048/AES-128 virus, make sure the removal of this virus has completed.
